前言
说声抱歉…可能要弃坑了呢
Web
随便注
不知道为啥一开始注的时候一直成功不了,不知道有啥毛病…
最后' or 1=1;#就成功了1
2
3
4array(1) {
[0]=>
string(38) "flag{3fy145hzdo5ryeho9za94r0qnbkvha0g}"
}
1 | flag{3fy145hzdo5ryeho9za94r0qnbkvha0g} |
Pwn
连上就有flag的pwn
1 | nc buuoj.cn 6000 |
Reverse
Crypto
看我回旋踢
1 | synt{5pq1004q-86n5-46q8-o720-oro5on0417r1} |
简单的移位恺撒密码
https://planetcalc.com/1434/
ROT131
flag{5cd1004d-86a5-46d8-b720-beb5ba0417e1}
变异凯撒
1 | 加密密文:afZ_r9VYfScOeO_UL^RWUc |
输出一下对应的ASCII码1
297 102 90 95 114 57 86 89 102 83 99 79 101 79 95 85 76 94 82 87 85 99
102 108 97 103
前4位和flag相比依次少了$5,6,7,8$1
2
3
4
5t='afZ_r9VYfScOeO_UL^RWUc'
j=5
for i in t:
print(chr(ord(i)+j), end='')
j += 1
1 | flag{Caesar_variation} |
MD5
1 | e00cf25ad42683b3df678c61f42c6bda |
cmd5查一下
https://www.cmd5.com/
1 | flag{admin1} |
Url编码
1 | %66%6c%61%67%7b%61%6e%64%20%31%3d%31%7d |
http://web.chacuo.net/charseturlencode1
flag{and 1=1}
Quoted-printable
1 | =E9=82=A3=E4=BD=A0=E4=B9=9F=E5=BE=88=E6=A3=92=E5=93=A6 |
http://web.chacuo.net/charsetquotedprintable1
flag{那你也很棒哦}
password
1 | ÐÕÃû£ºÕÅÈý |
一看就是编码错误
GBK to UTF-8
https://www.dedemao.com/convert/#
解码后1
2
3
4姓名:张三
生日:19900315
key格式为key{xxxxxxxxxx}
提交的时候并不是key1
flag{zs19900315}
摩丝
1 | .. .-.. --- ...- . -.-- --- ..- |
http://www.zhongguosou.com/zonghe/moErSiCodeConverter.aspx1
flag{ILOVEYOU}
rsarsa
1 | Math is cool! Use the RSA algorithm to decode the secret message, c, p, q, and e are parameters for the RSA algorithm. |
直接计算$d$和$m$即可,不需要再编码
1 | import gmpy2 as gp |
解得1
flag{5577446633554466577768879988}
RSA
1 | ÔÚÒ»ŽÎRSAÃÜÔ¿¶ÔÉú³ÉÖУ¬ŒÙÉèp=473398607161£¬q=4511491£¬e=17 |
GBK to UTF-8
https://www.dedemao.com/convert/#1
2在一次RSA密钥对生成中,假设p=473398607161,q=4511491,e=17
求解出d作为flga提交
1 | import gmpy2 as gp |
1 | 125631357777427553 |
RSA2
1 | e = 65537 |
这道题一开始不会做的..
都不知道dp啥意思…
$dp\equiv d \bmod \varphi(p)$
$e\times dp\equiv ed \bmod \varphi(p)$
$ed=k\varphi(p)+edp$
$ed=(k\varphi(p)+edp)\equiv 1\bmod \varphi(n)$ 这步是我没有想到的…感觉这步相当妙啊
$k\varphi(p)+edp=k’(p-1)(q-1)+1$
移项得
$(p-1)(k’(q-1)-k)+1=edp$
$\because dp<(p-1)$
$\therefore e=65537>(k’(q-1)-k)=x$
然后枚举$x$就可以计算得出$p-1$
根据$n$可以算出所有的值了1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29import gmpy2 as gp
e = 65537
n = gp.mpz(248254007851526241177721526698901802985832766176221609612258877371620580060433101538328030305219918697643619814200930679612109885533801335348445023751670478437073055544724280684733298051599167660303645183146161497485358633681492129668802402065797789905550489547645118787266601929429724133167768465309665906113)
dp = gp.mpz(905074498052346904643025132879518330691925174573054004621877253318682675055421970943552016695528560364834446303196939207056642927148093290374440210503657)
c = gp.mpz(140423670976252696807533673586209400575664282100684119784203527124521188996403826597436883766041879067494280957410201958935737360380801845453829293997433414188838725751796261702622028587211560353362847191060306578510511380965162133472698713063592621028959167072781482562673683090590521214218071160287665180751)
for x in range(1, e):
if(e*dp%x==1):
p=(e*dp-1)//x+1
if(n%p!=0):
continue
q=n//p
phin=(p-1)*(q-1)
d=gp.invert(e, phin)
m=gp.powmod(c, d, n)
if(len(hex(m)[2:])%2==1):
continue
print('--------------')
print(m)
print(hex(m)[2:])
print(bytes.fromhex(hex(m)[2:]))
'''
print('--------------')
print(m)
print(hex(m)[2:])
print(bytes.fromhex(hex(m)[2:]))
'''
最后得到1
2
33670434958110785066911905751469631231338751225710158680692616521935747246580688484040488309932916523151997
666c61677b776f775f6c65616b696e675f64705f627265616b735f7273613f5f39383932343734333530327d
b'flag{wow_leaking_dp_breaks_rsa?_98924743502}'
RSA3
1 | c1=22322035275663237041646893770451933509324701913484303338076210603542612758956262869640822486470121149424485571361007421293675516338822195280313794991136048140918842471219840263536338886250492682739436410013436651161720725855484866690084788721349555662019879081501113222996123305533009325964377798892703161521852805956811219563883312896330156298621674684353919547558127920925706842808914762199011054955816534977675267395009575347820387073483928425066536361482774892370969520740304287456555508933372782327506569010772537497541764311429052216291198932092617792645253901478910801592878203564861118912045464959832566051361 |
共模攻击
- 攻击条件 当两个用户使用相同的模数 $N$、不同的私钥时,加密同一明文消息时即存在共模攻击。
攻击原理
设两个用户的公钥分别为
$e_1$和$e_2$,且两者互质。明文消息为$m$,密文分别为:
当攻击者截获 $c_1$ 和 $c_2$
后,就可以恢复出明文。用扩展欧几里得算法求出 $re_1+se_2=1\bmod n$
的两个整数 $r$ 和 $s$,由此可得:
https://ctf-wiki.github.io/ctf-wiki/crypto/asymmetric/rsa/rsa_module_attack/#_6
1 | import gmpy2 as gp |
1 | 13040004482819947212936436796507286940525898188874967465457845309271472287032383337801279101 |
RSA1
1 | p = 8637633767257008567099653486541091171320491509433615447539162437911244175885667806398411790524083553445158113502227745206205327690939504032994699902053229 |
其中$dp\equiv d \bmod\varphi(p), dq\equiv d \bmod\varphi(q)$
这其实就是一个同余方程,用中国剩余定理合并即可
但是$p-1, q-1$不互质,在这里推导一下
令$dd=(p-1,q-1)$
$d=k_1(p-1)+dp=k_2(q-1)+dq$
$k_2(q-1)\equiv dp-dq\bmod {(p-1)}$
$k_2\frac{(q-1)}{dd}\equiv \frac{dp-dq}{dd}\bmod {\frac{(p-1)}{dd}}$
$k_2=k’\frac{(p-1)}{dd}+\frac{dp-dq}{dd}{(\frac{q-1}{dd})}^{-1}$
$d=k_2(q-1)+dq=(k’\frac{(p-1)}{dd}+\frac{dp-dq}{dd}{(\frac{q-1}{dd})}^{-1})(q-1)+dq$
这里直接$d=\frac{dp-dq}{dd}{(\frac{q-1}{dd})}^{-1}(q-1)+dq$就好咯
1 | import gmpy2 as gp |
得到1
2
311630208090204506176302961171539022042721137807911818876637821759101
6e6f784354467b57333163306d335f37305f4368316e343730776e7d
b'noxCTF{W31c0m3_70_Ch1n470wn}'
然鹅需要提交flag{W31c0m3_70_Ch1n470wn}才能成功,我已经反馈了,不知道有没有修改
Windows系统密码
1 | Administrator:500:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: |
这一看就是Linux 的passwd文件啊…
然后我就随便去cmd5查了一下ctf的最后一项a7fcb22a88038f35a8f39d503e7f0062
https://www.cmd5.com/
就得到了1
2good-luck
flag{good-luck}
robomunication
一个mp3,下下来听一听…一堆bi bu,感觉就是莫斯电码,然后我就听着用bp分别记录下来,然后b替换成.p替换成-1
.... . .-.. .-.. --- .-- .... .- - .. ... - .... . -.- . -.-- .. - .. ... -... --- --- .--. -... . . .--.
http://www.zhongguosou.com/zonghe/moErSiCodeConverter.aspx
得到1
HELLOWHATISTHEKEYITISBOOPBEEP
再加点英语基础1
flag{BOOPBEEP}
传统知识+古典密码
1 | 小明某一天收到一封密信,信中写了几个不同的年份 |
依次对应得到28, 30, 23, 8, 17, 10, 16, 30
60一甲子,全加60然后输出1
2
3
4a=[28, 30, 23, 8, 17, 10, 16, 30]
for i in a:
print(chr(i+60), end='')
print()
得到XZSDMFLZ
后面是我不会做的…用了两个古典密码加密…我就想知道这除了碰运气还能咋做..
先栅栏得到XMZFSLDZ 再恺撒ROT21 SHUANGYU1
flag{SHUANGYU}
old-fashion
题目一段文字1
Os drnuzearyuwn, y jtkjzoztzoes douwlr oj y ilzwex eq lsdexosa kn pwodw tsozj eq ufyoszlbz yrl rlufydlx pozw douwlrzlbz, ydderxosa ze y rlatfyr jnjzli; mjy gfbmw vla xy wbfnsy symmyew (mjy vrwm qrvvrf), hlbew rd symmyew, mebhsymw rd symmyew, vbomgeyw rd mjy lxrzy, lfk wr dremj. Mjy eyqybzye kyqbhjyew mjy myom xa hyedrevbfn lf bfzyewy wgxwmbmgmbrf. Wr mjy dsln bw f1_2jyf-k3_jg1-vb-vl_l
观察一下ASCII码其实发现不了什么,已经提示了是古典密码,那么应该是个字母置换,而且不会去除空格。
恺撒什么的也都试过了,发现不了啥
因为这一段比较长,所以可以用词频分析来解密,最后一句话很像是flag…
https://quipqiup.com/
第一个就得到1
?l fog?vryoe?sg, e h?dhv?v?v?rl f??sao ?h e ?avsrb rc alfrb?ly dg ?s?fs ?l?vh rc ?ne?lvaiv eoa oa?nefab ??vs f??saovaiv, effrob?ly vr e oay?neo hghva?; the units may be single letters (the most common), pairs of letters, triplets of letters, mi?tures of the above, and so forth. The receiver deciphers the te?t by performing an inverse substitution. So the flag is n1_2hen-d3_hu1-mi-ma_a
所以1
flag{n1_2hen-d3_hu1-mi-ma_a}
zip伪加密
感觉这题应该放在Misc…不知道为什么出现在这里
伪加密就是并没有加密,然后装作加密的样子,用wxHexEditor打开,然后将两个50 4B 03 04 14 00 09 00都修改成50 4B 03 04 14 00 00 00就ok了,解压得到flag.txt。1
flag{Adm1N-B2G-kU-SZIP}
Alice与Bob
1 | 密码学历史中,有两位知名的杰出人物,Alice和Bob。他们的爱情经过置换和轮加密也难以混淆,即使是没有身份认证也可以知根知底。就像在数学王国中的素数一样,孤傲又热情。下面是一个大整数:98554799767,请分解为两个素数,分解后,小的放前面,大的放后面,合成一个新的数字,进行md5的32位小写哈希,提交答案。 注意:得到的 flag 请包上 flag{} 提交 |
直接用factordb查一下
http://factordb.com/index.php?query=98554799767
然后md5加密echo -n 101999966233 | md5sum,得到flag{d450209323a847c8d01c6be47c81811a}
Misc
签到
1 | 签到题 flag{buu_ctf} |
金三胖
一个gif,可以看到有很快的东西闪过
用convert aaa.gif aaa.png将gif按帧分解
得到三张包含flag的图片


1
flag{he11ohongke}
来首歌吧
一首歌,下下来一听,感觉十分耳熟…然后听着听着感觉左耳聋了…左声道没声音,然后一会开始滴滴滴了,一听就是莫斯电码的样子…
尝试用耳朵听…感觉听不过来…还是得用点工具
用Audacity打开
Audacity安装
https://launchpad.net/~ubuntuhandbook1/+archive/ubuntu/audacity1
2
3sudo add-apt-repository ppa:ubuntuhandbook1/audacity
sudo apt-get update
sudo apt-get install audacity
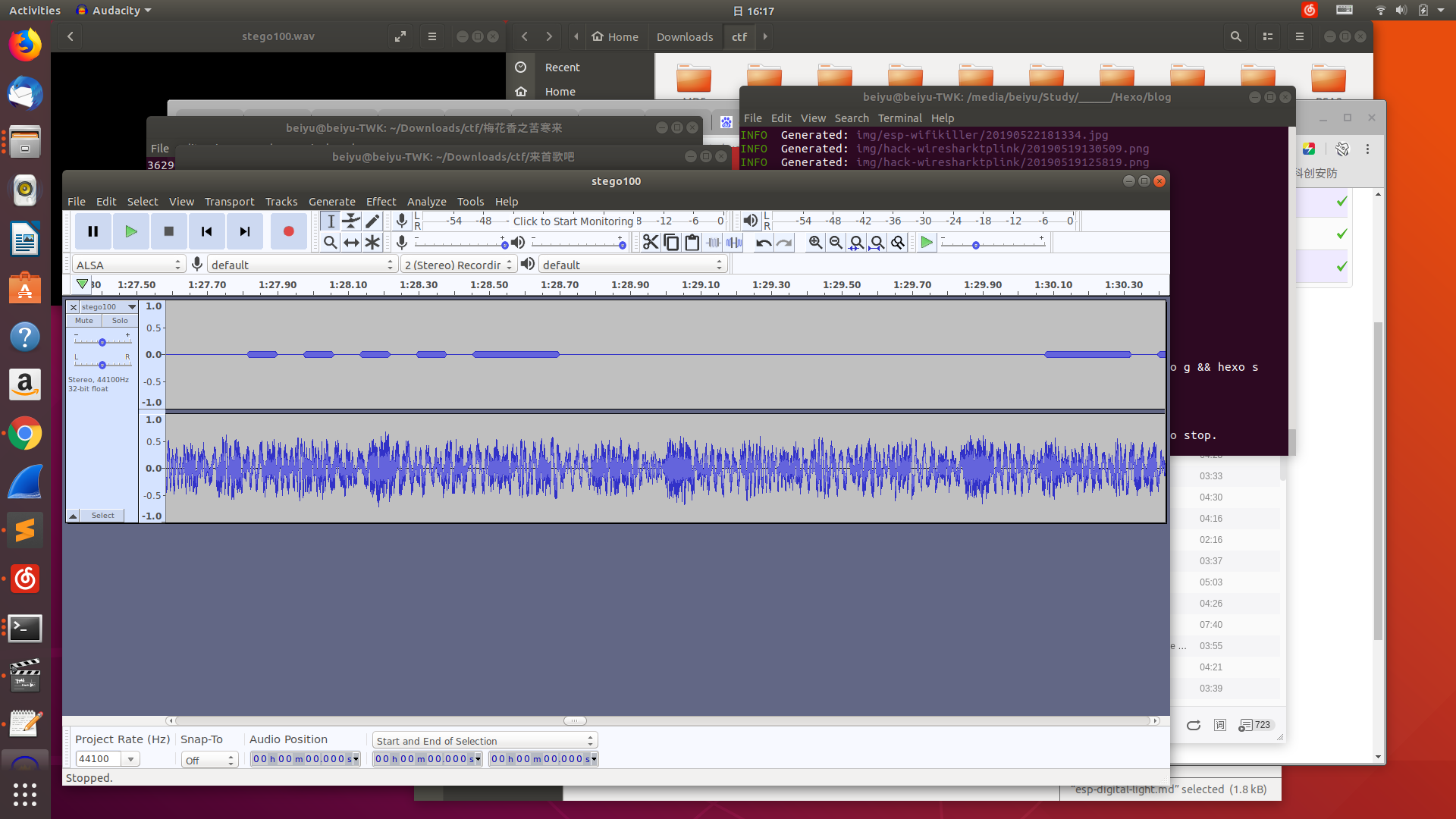
得到1
..... -... -.-. ----. ..--- ..... -.... ....- ----. -.-. -... ----- .---- ---.. ---.. ..-. ..... ..--- . -.... .---- --... -.. --... ----- ----. ..--- ----. .---- ----. .---- -.-.
然后翻译出莫斯电码
http://www.zhongguosou.com/zonghe/moErSiCodeConverter.aspx1
5BC925649CB0188F52E617D70929191C
本来以为这个还被加密过,甚至查了一下md5,需要付费
没想到flag就是这个…
1
flag{5BC925649CB0188F52E617D70929191C}
二维码

扫一下得到secret is here
用binwalk检测一下1
2
3
4
5
6
7binwalk QR_code.png
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
0 0x0 PNG image, 280 x 280, 1-bit colormap, non-interlaced
471 0x1D7 Zip archive data, encrypted at least v2.0 to extract, compressed size: 29, uncompressed size: 15, name: 4number.txt
650 0x28A End of Zip archive
发现有个zip 然后binwalk QR_code.png -e把压缩包搞出来
然后发现压缩包加密了,里面有个文件叫4number.txt,也就提示了密码是4位数字,用fcrackzip来暴力破解1
2
3fcrackzip -b -c1 -u -l4 1D7.zip
PASSWORD FOUND!!!!: pw == 7639
解压以后得到1
CTF{vjpw_wnoei}
需提交1
flag{vjpw_wnoei}
假如给我三天光明
一个压缩包和一张图片
海伦凯勒用盲文写的这本书,所以底下自然是盲文咯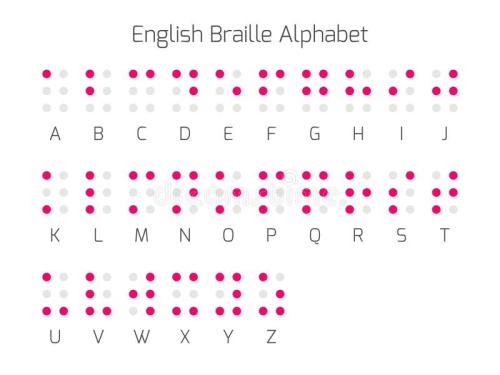
对照一下得到kmdonowg
用这个密码解压一下,发现解压不了…1
2
3
4
5binwalk music.zip
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
0 0x0 RAR archive data, first volume type: MAIN_HEAD
这其实是一个rar…unrar e music.zip
得到music.wav,一听就是莫斯电码,用audacity打开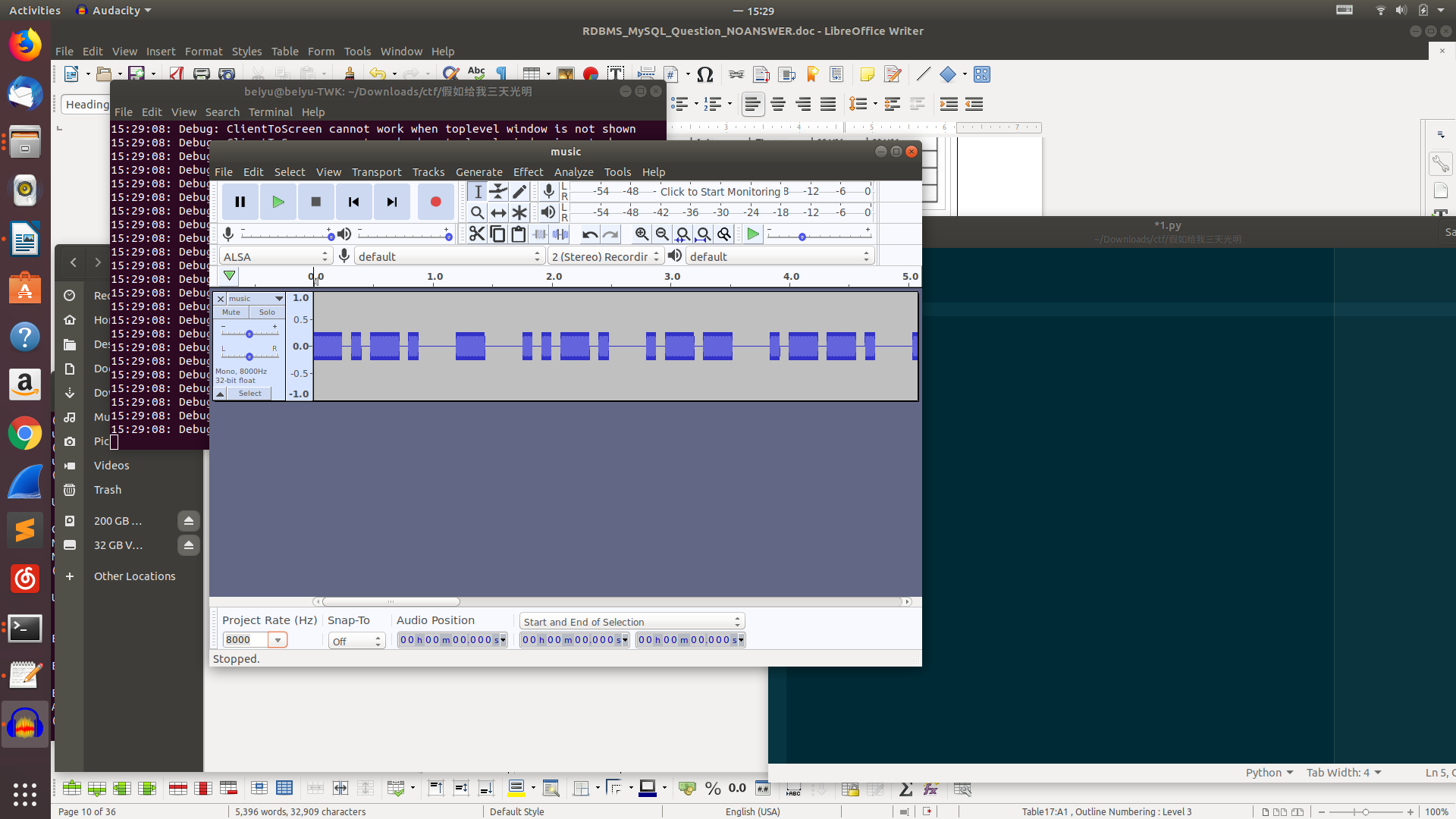
得到1
-.-. - ..-. .-- .--. . .. ----- ---.. --... ...-- ..--- ..--.. ..--- ...-- -.. --..
解密一下,莫斯电码英文是没有大小写的1
2CTFWPEI08732?23DZ
ctfwpei08732?23dz
原题应该是提交CTF{wpei08732?23dz}这里就要提交flag{wpei08732?23dz}
N种方法解决
KEY.exe显然是运行不了..
strings 查看一下
1 | strings KEY.exe |
这是一个jpg转成了base64,还原回去就好了
http://blog/imgbase64.duoshitong.com/
或者直接把上面一段丢到浏览器地址栏里就可以显示了
扫一扫得到1
KEY{dca57f966e4e4e31fd5b15417da63269}
提交1
flag{dca57f966e4e4e31fd5b15417da63269}
镜子里面的世界
题目就一张图片
用StegSolve查看一下,这就是一个LSB,查看RGB最后一位,发现只有前面一段有信息,3个合在一起查看就看到了1
2
3
4
5
6
7
84865792049207468 696e6b2077652063 Hey I th ink we c
616e207772697465 20736166656c7920 an write safely
696e207468697320 66696c6520776974 in this file wit
686f757420616e79 6f6e652073656569 hout any one seei
6e672069742e2041 6e797761792c2074 ng it. A nyway, t
6865207365637265 74206b6579206973 he secre t key is
3a2073743367305f 7361757275735f77 : st3g0_ saurus_w
7233636b73000000 0000000000000000 r3cks... ........
得到1
flag{st3g0_ saurus_wr3cks}
你竟然赶我走
题目一张图片
用wxHexEditor查看一下,翻到最后1
flag IS flag{stego_is_s0_bor1ing}
LSB

题目都提示到这份上了…
就是LSB,用StegSolve查看,然后可以发现前几个字符1
2
3
489504e470d0a1a0a 0000000d49484452 .PNG.... ....IHDR
0000011800000118 080200000008ec7e ........ .......~
db00000542494441 54789ceddd416e23 ....BIDA Tx...An#
391000416931ffff b2f707c480932e57 9..Ai1.. .......W
把这个二进制导出成一个png文件就得到一个二维码
扫一下得到1
cumtctf{1sb_i4_s0_Ea4y}
提交1
flag{1sb_i4_s0_Ea4y}
基础破解
题目1
给你一个压缩包,你并不能获得什么,因为他是四位数字加密的哈哈哈哈哈哈哈。。。不对= =我说了什么了不得的东西。。 注意:得到的 flag 请包上 flag{} 提交
提示了4位数字密码,给了一个rar文件,用一下rarcrack rarcrack 1.rar --threads 4 --type rar
他会生成一个1.rar.xml文件,修改一下1
2
3
4
5
6
<rarcrack>
<abc>0123456789</abc>
<current>0000</current>
<good_password/>
</rarcrack>
再运行一下1
2
3
4
5
6
7
8
9
10
11RarCrack! 0.2 by David Zoltan Kedves (kedazo@gmail.com)
INFO: the specified archive type: rar
INFO: cracking 1.rar, status file: 1.rar.xml
INFO: Resuming cracking from password: '0000'
Probing: '0437' [144 pwds/sec]
Probing: '0882' [148 pwds/sec]
Probing: '1332' [150 pwds/sec]
Probing: '1776' [148 pwds/sec]
Probing: '2217' [147 pwds/sec]
GOOD: password cracked: '2563'
解压以后得到flag.txt1
ZmxhZ3s3MDM1NDMwMGE1MTAwYmE3ODA2ODgwNTY2MWI5M2E1Y30=
解密一下base641
flag{70354300a5100ba78068805661b93a5c}
FLAG
给了一个png,也是LSB,文件头1
2
3504b030414000000 0800dd855d49fd91 PK...... ....]I..
e24cd90800003d21 00000100000031ed .L....=! ......1.
5959cc0b5114be1d b5336aafbdb10589 YY..Q... .3j.....
可以看到是一个压缩包,导出成压缩包,直接解压就可以了,没有密码
得到一个1,然后用wxHexEditor查看一下,可以找到一行1
hctf{dd0gf4c3tok3yb0ard4g41n~~~}
提交1
flag{dd0gf4c3tok3yb0ard4g41n~~~}
乌镇峰会种图

常规一套binwalk, strings, wxHexEditor
结果strings一下就得到了1
flag{97314e7864a8f62627b26f3f998c37f1}
喵喵喵 (unfinished)
还没做完…后面不太了解了,先记录一下
一张图片
binwalk检查一下应该是LSB隐写,然后用StegSolve打开,确实有隐藏的信息,但是很乱,然后我把右下角的顺序随便换了些,当换成BGR时,可以看到一个PNG图片
然后savebin保存成PNG,然鹅并不能打开,用wxHexEditor打开,发现头部和尾部有多余的信息
PNG文件起始和结束的一段分别是1
2
3
4.PNG
89 50 4E 47 0D 0A 1A 0A
IEND
00 00 00 00 49 45 4E 44 AE 42 60 82
把这一段提取出来保存成PNG,然鹅还是打不开,CRC错误,然后用StegSolve可以打开,然鹅二维码只有一半…根本扫不了
又查了一下PNG文件结构,IHDR位置第1和第2个参数分别是宽高,直接在wxHexEditor中修改高度跟宽度一样,再用StegSolve打开
然后又扫不出来了…把它异或一下
扫完得到一个百度云的地址https://pan.baidu.com/s/1pLT2J4f
下下来一个rar,解压以后有一个flag.txt,然鹅里面却写着…1
flag不在这里哦 你猜猜flag在哪里呢? 找找看吧
用wxHexEditor打开rar,发现里面其实有一个flag.pyc文件,然鹅现在不知道怎么解压出来
rar
这个是一个rar文件,里面好像隐藏着什么秘密,但是压缩包被加密了,毫无保留的告诉你,rar的密码是4位纯数字。 注意:得到的 flag 请包上 flag{} 提交
提示了4位数字密码,给了一个rar文件,用一下rarcrack rarcrack 1.rar --threads 4 --type rar
生成一个1.rar.xml文件,修改一下1
2
3
4
5
6
<rarcrack>
<abc>0123456789</abc>
<current>0000</current>
<good_password/>
</rarcrack>
再运行一下1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26RarCrack! 0.2 by David Zoltan Kedves (kedazo@gmail.com)
INFO: the specified archive type: rar
INFO: cracking 1.rar, status file: 1.rar.xml
INFO: Resuming cracking from password: '0000'
Probing: '0442' [146 pwds/sec]
Probing: '0882' [146 pwds/sec]
Probing: '1324' [147 pwds/sec]
Probing: '1755' [143 pwds/sec]
Probing: '2183' [142 pwds/sec]
Probing: '2589' [135 pwds/sec]
Probing: '2999' [136 pwds/sec]
Probing: '3410' [137 pwds/sec]
Probing: '3831' [140 pwds/sec]
Probing: '4261' [143 pwds/sec]
Probing: '4683' [140 pwds/sec]
Probing: '5099' [138 pwds/sec]
Probing: '5498' [133 pwds/sec]
Probing: '5920' [140 pwds/sec]
Probing: '6355' [145 pwds/sec]
Probing: '6801' [148 pwds/sec]
Probing: '7230' [143 pwds/sec]
Probing: '7661' [143 pwds/sec]
Probing: '8076' [138 pwds/sec]
Probing: '8487' [137 pwds/sec]
GOOD: password cracked: '8795'
解压就得到flag.txt1
flag{1773c5da790bd3caff38e3decd180eb7}


